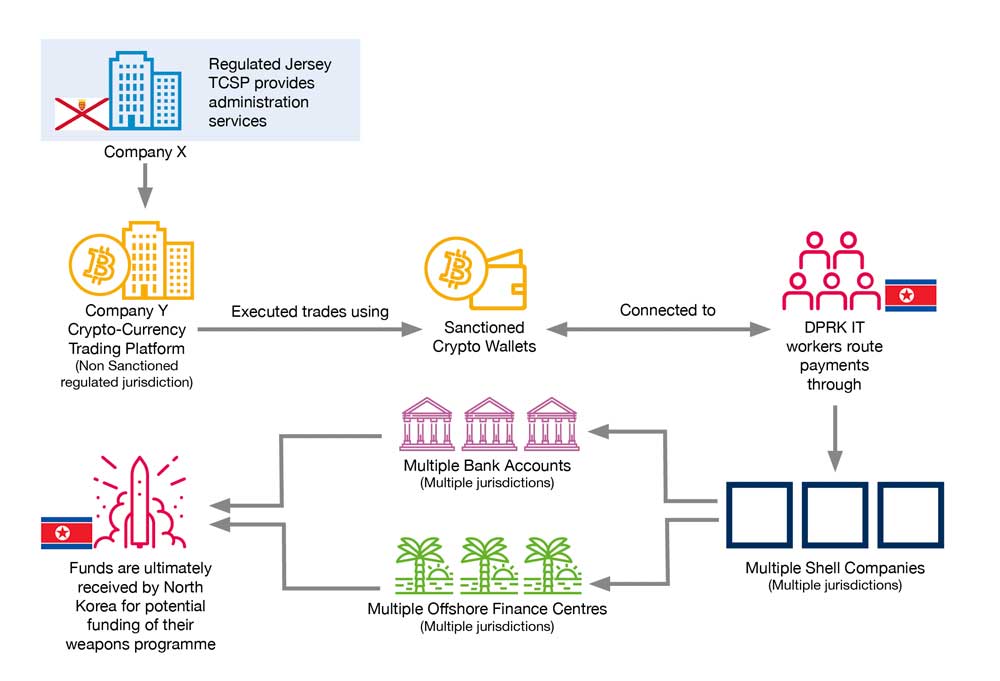
Company X, a regulated Jersey Trust Company Service Provider (TCSP), has provided administrative services to Company Y. Company Y, a crypto-currency trading platform, was registered in a non-sanctioned and well-regulated jurisdiction. It was identified that trades executed by Company Y, involved sanctioned wallets connected to Democratic People’s Republic of Korea (DPRK) IT workers.
The DPRK IT workers had used stolen or borrowed identities to secure remote work positions and utilised Virtual Private Networks (VPNs), Virtual Private Servers (VPSs), and Remote Desktop applications to obscure their true locations, making it appear as though they were based in non-sanctioned jurisdictions.
These methods helped bypass traditional banking systems and reduced the risk of detection. Funds were transferred through multiple accounts and jurisdictions, involving offshore finance centres, to further obscure their origins. Shell companies and front entities were used to facilitate these transactions, making it difficult to trace the money back to North Korea.
DPRK IT workers, posing as freelance third-country nationals, are employed by companies worldwide, including those in the UK and the US. These workers generate significant revenue for the North Korean regime, which is then laundered through complex financial networks to evade international sanctions.
PF refers to the provision of funds or resources to support the development, production, or acquisition of weapons of mass destruction (WMD), including nuclear, chemical, and biological weapons. This type of financing can occur through various means, such as legal or illegal financial transactions, support from state or non-state actors, and the exploitation of financial systems to disguise the true purpose of the funds.
Proliferation financing poses significant threats to global security, as it enables states or organisations to advance their capacities to develop harmful weaponry that can be used for aggression against other nations or in terrorist activities. To combat this threat, many countries and international organizations implement strict regulations and monitoring systems designed to prevent and disrupt the flow of funds intended for proliferation purposes. This includes measures such as enhanced due diligence by financial institutions and stricter compliance with anti-money laundering (AML) and counter-terrorism financing (CTF) policies.
Frauds and scams are deceptive practices aimed at tricking individuals or organisations into giving up their money, personal information, or property.
Fraud typically involves a deliberate misrepresentation of the truth or concealment of essential facts to gain an unfair advantage. It can take many forms, such as identity theft, financial fraud, and investment scams. In these situations, the perpetrator usually uses false statements or fake documents to create a false impression, leading the victim to make decisions that result in financial loss.
Scams, are often more casual and can involve a wide range of schemes that aim to con people out of their money. Common types of scams include phishing emails that impersonate legitimate organisations to steal passwords or credit card information, lottery or prize scams that promise money in exchange for upfront fees, and romance scams that exploit emotional connections to gain financial support.
Both frauds and scams can have devastating effects on individuals and communities, leading to financial hardship and emotional distress. It’s important to stay informed and vigilant to protect indivdiuals and organisations from falling faul of their targetted attempts of deception and trickery.
We continually strive to enhance the quality of the products we produce, from our typologies to reports, Insight papers to training guides. However, we can only improve if you share your feedback with us about what you think about them. This is your chance to let us know and we appreciate it your feedback. Click the navy button below or scan the QR code.
Tell us what you think >.svg)